My friend and neighbor, Justin Graves, gave me a very thoughtful gift this Christmas. The initial gift was a printed Space Invader, as seen here.
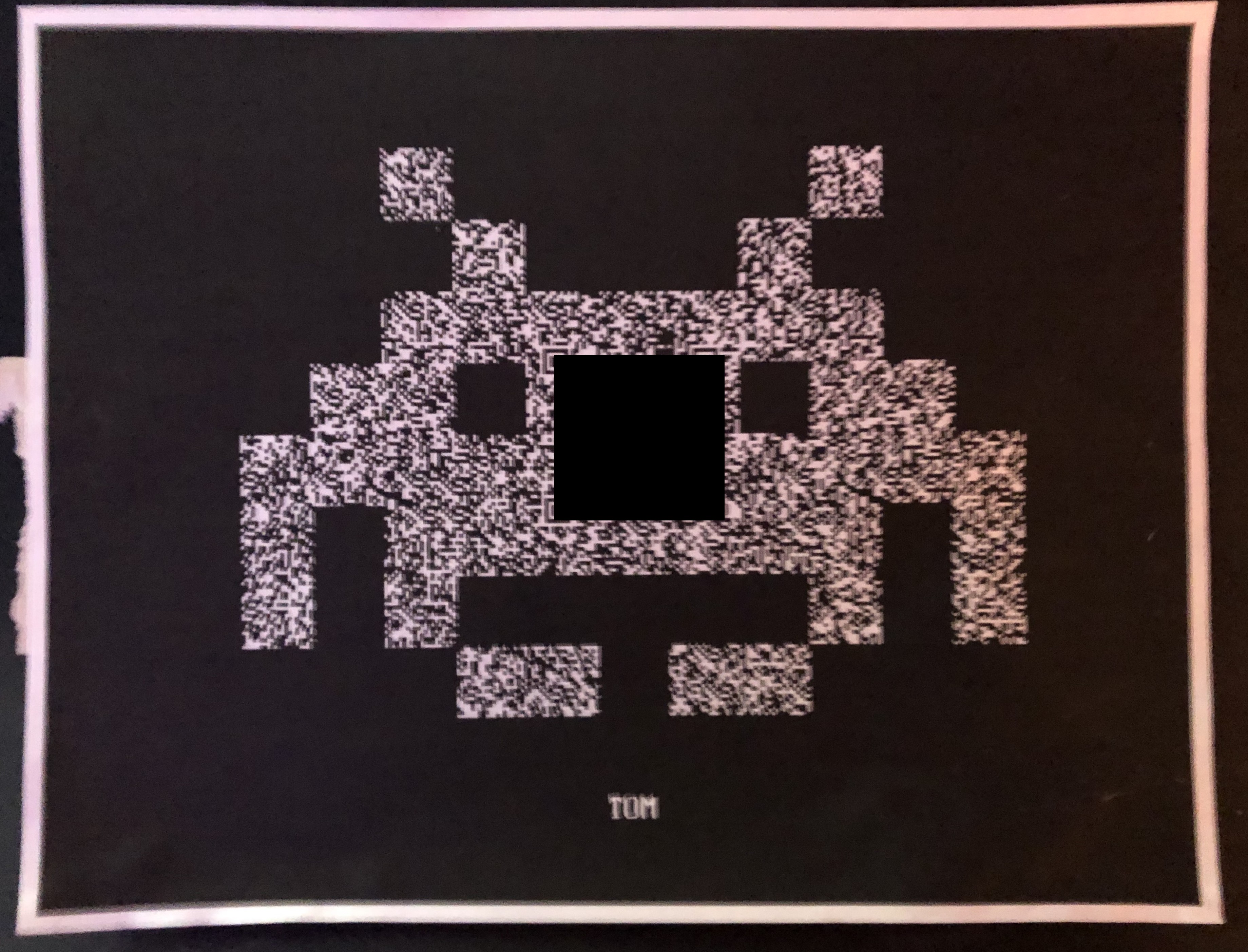
I’ve obfuscated the center of the image with a black box. The Invader is textured with a random static pattern. On closer inspection, I could see the Position and Alignment patterns of a typical QR Code. Scanning this code with my phone generated a long list of seemingly random letters. A PUZZLE! This looks like the entry point to a hacking puzzle, also known as a CTF. Fun!
So, what next? My initial thought, based on the length of the string, was that this was a hash. However, after seeing that only alpha characters were used, and there was a mix of upper- and lower-cased letters, I figured that this was just encoded data, likely base64. Using an online base64 decoder, I was greeted with a human-readable message (again, obfuscated).
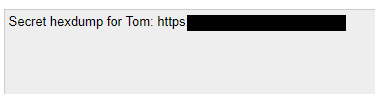
After visiting the encoded URL, and entering the provided, code, I was shown the output of a hex dump, some of which can be seen here.
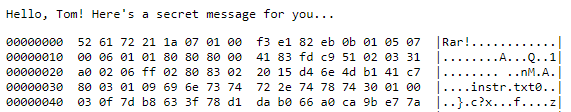
This is the output of the hexdump tool common in UNIX-like systems. Typically, this is used to show the hexadecimal (and ASCII) representation of binary data. The “Rar!” at the top, and the initial signature “52 61” indicates that this is probably a hexdump for a RAR file, which is a common compressed file format. Using the HxD hex editor, I was able to save the hex dump as an actual RAR file. Curiously, it asked for a password, which I didn’t have.
Closer inspection of the hex dump web page revealed a possible password within the source code, as seen here. The password was hidden within an HTML comment tag.
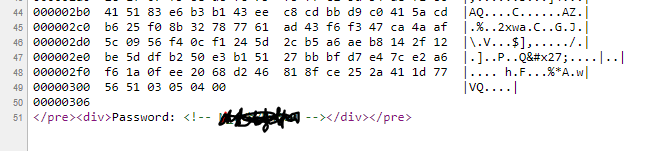
This password granted access to two files in the RAR archive, “instr.txt” and “key.”
The “key” file contains an ssh private key, and the “instr.txt” file contains instructions, indicating that the private key is encrypted with a specific password. The file also contains a haiku, and an indication that a “server” can be found with a “hipku.” Obfuscated instructions can be seen here.
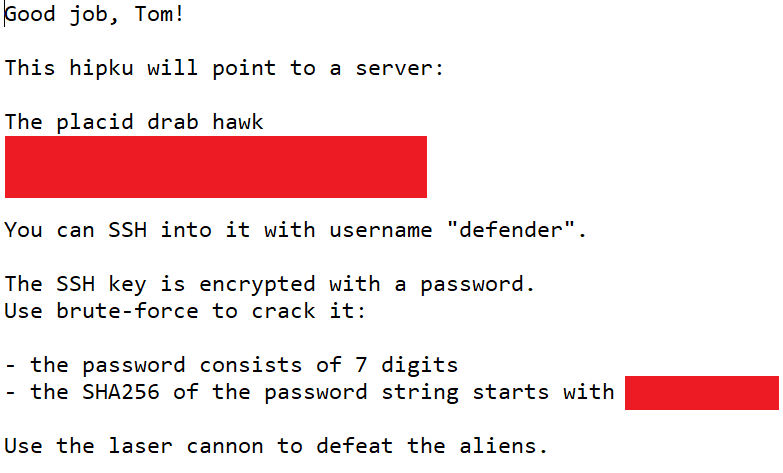
I hadn’t heard of a “hipku” before, but a Google search pointed me to Hipku, a cool project that allows you to encode an IP address as a haiku! Pasting the included “haiku” into the Hipku site revealed an IP address. So, we have a server IP address, a username, and a private key. We now need to figure out the password to the private key. From the hints, we know that the password is comprised of 7 digits. We also have the first 11 characters of the SHA-2 hash digest of the password.
How to we find the password? Since the password is comprised of 7 digits, then there are only about 9 million possible passwords, which, to a password cracker, is nothing.
I wrote this quick and dirty Python script, which quickly loops through all of the possible passwords in under 10 seconds.
import sys
import os
import hashlib
for password in range(0,9999999):
if hashlib.sha256(str(password).encode('utf-8')).hexdigest()[:11] == '[OBFUSCATED]':
print(password)This script has some flaws. Notably, a valid 7 digit password with leading zeroes will not be discovered, since I am not padding numbers under 1 million. I just hoped that the resulting password would be outside of that range. ? Luckily, a single password candidate was revealed with my script! This password, along with the “defender” username and the private key, allowed me to successfully login to the server using SSH, as seen here:
After hitting the space bar, I am greeted with a console version of Space Invaders.
I was never good at Space Invaders, but this version is very forgiving. After defeating all of the Invaders, I was greeted with a Congratulations and a personal message from Justin.
This was a fun and rewarding CTF-like puzzle! Thanks Justin, and Merry Christmas!
Tom, I’m so happy that you enjoyed this! When Santa was asking what you might like for Christmas, I told him … “the man needs something he can decode!” Looks like Santa got it right this time. I was a little nervous that it would be a pain … but seeing the process and the thoughts behind the experience of decoding this … it was priceless. I had a feeling you’d appreciate something so intricate. Thanks for teaching me a little bit along the way, too.
Merry Christmas, my friend!
-JG